作者你可以帮我设置Strongtwan吗...
不一定有空回复任何问题,看到留言会回复;或者留下邮箱,后续看到也会进行回复。...
还有 21 人发表了评论 加入19746人围观不一定有空回复任何问题,看到留言会回复;或者留下邮箱,后续看到也会进行回复。...
还有 21 人发表了评论 加入19746人围观

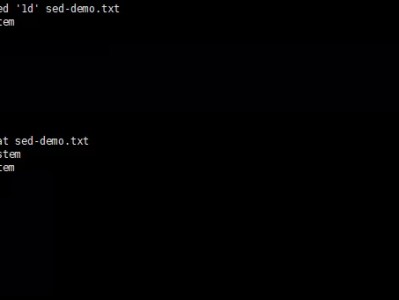
sed 命令指的是”Stream EDitor”,用来实现 Linux 系统基本的文本转换。

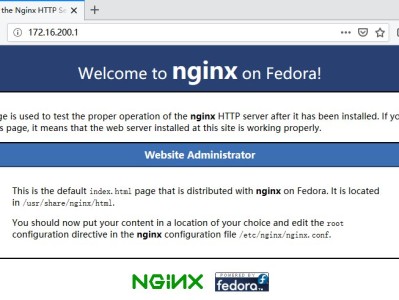
软件库(简称为repo)是一个软件包文件的中心存储区,用户可以通过该软件库更新自己的系统软件。
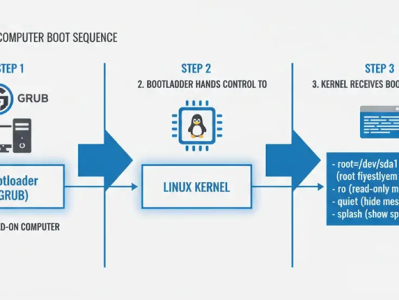
Linux 系统的启动过程相较于其他操作系统略为复杂,其内核在启动过程中可以接受众多参数的控制。通过启动命令行,就可以在系统启动时为内核提供众多初始信息。
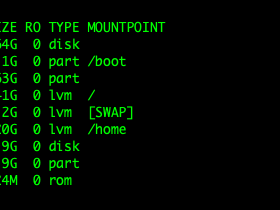
Linux 系统使用 USB 驱动器,正确的卸载和移除驱动器以防止数据丢失或损坏显得非常重要。简单地拔掉驱动器而不正确卸载它可能会导致问题造成数据丢失或 USB 驱动器损坏。
ISO

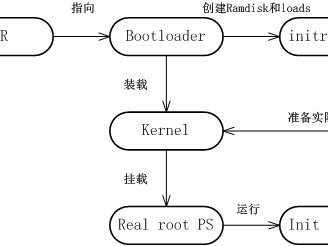
操作系统